I'm Eyosiyas Eyasu
- Network Security Engineer
- Bug Bounty Hunter
- Web Developer

About Me.
Hi, I’m Eyosiyas, a passionate cybersecurity professional with a focus on network security, web pentesting, and reverse engineering. Over the years, I’ve developed a strong foundation in programming with C/C++ and Python, and I’m continuously expanding my expertise in threat detection and rootkit development. I enjoy diving into complex security challenges, whether it’s creating custom Web Application Firewalls (WAF) or building Network Intrusion Detection Systems (NIDS). My work is driven by a desire to build secure, efficient solutions, and I’m currently working on a project to develop a custom reverse proxy for our WAF.
In addition to my technical pursuits, I find great satisfaction in sharing my knowledge with others, whether through blog posts or by organizing Capture the Flag (CTF) competitions. When I'm not immersed in coding or security research, I enjoy strategic games and constantly seeking ways to sharpen my problem-solving skills. If you’d like to collaborate or discuss anything security-related, feel free to reach out!
Experience
- Network Intrusion Detection System (NIDS) Team Project | Aug 2024 - Present
- Custom Web Application Firewall (WAF) Team Project | Aug 2024 - Present
- ALX Hackathon Participant Completed | July
- CCNA NetAcad Certification Cisco | Completed | July 2024
- Cyber Talent Certificate Completed | December 2023
- Udacity Certifications Completed | August 2024
Awards
Skills
- Network Security
- Reverse Engineering
- Web Application Penetration Testing
- CTF Player
- Rootkit Development
- Python
- C
- Assembly Language
- Team Leader
- Github Project Management
Certifications
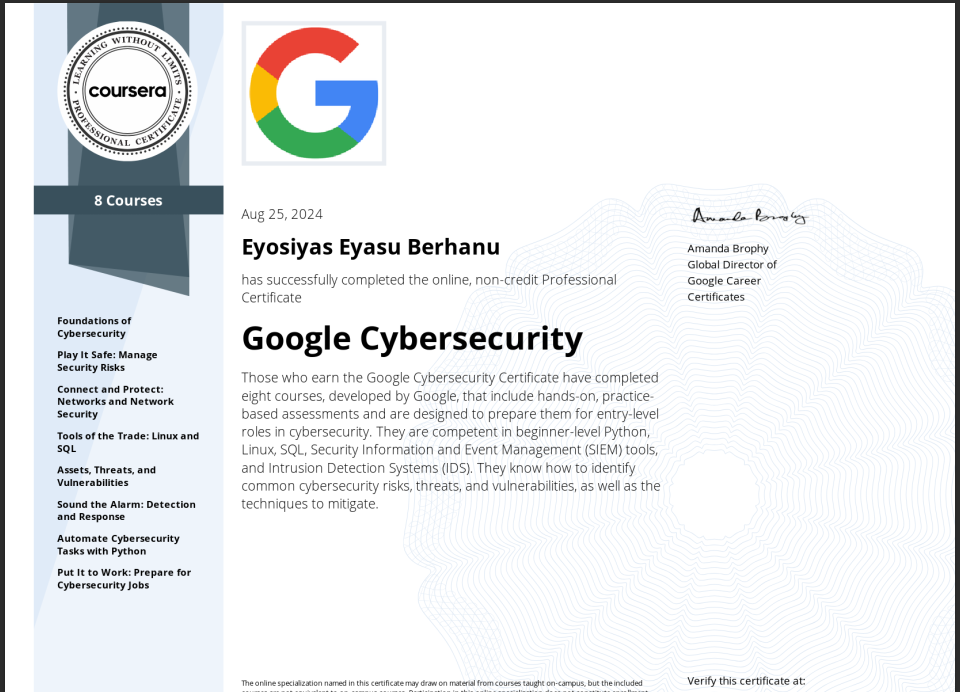
Google Professional Certificate
These certifications highlight your expertise in specific technical topics, such as cybersecurity and IT management, as recognized by Google and Coursera.
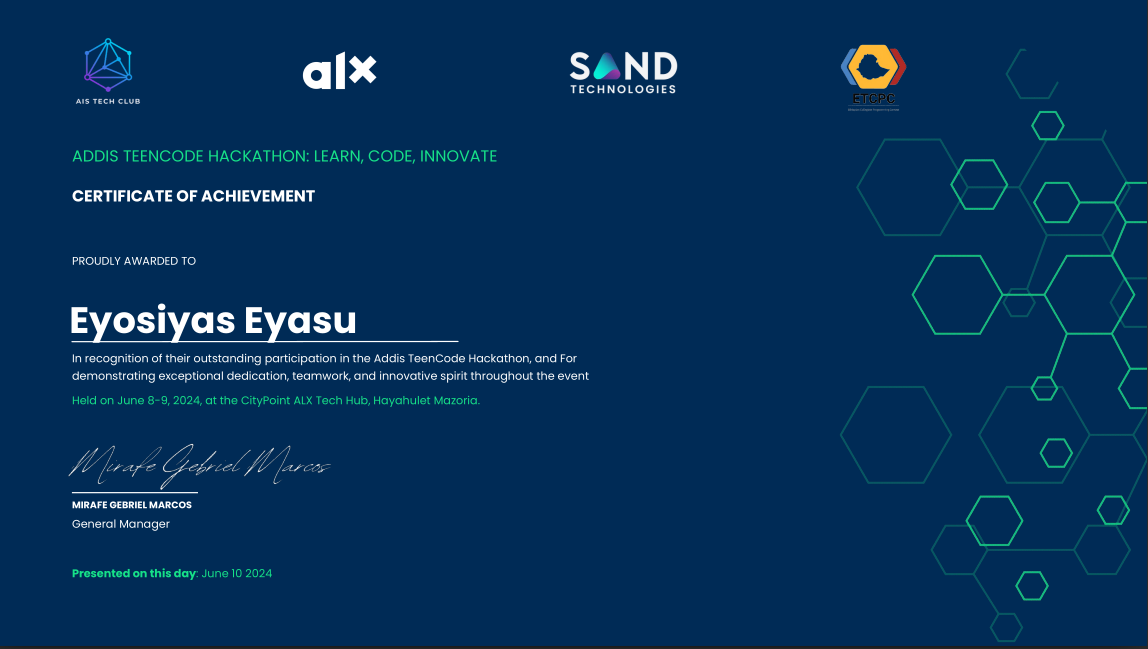
Addis Teencode Hackathon
A certificate of accomplishment for successfully completing a rigorous hackathon, demonstrating teamwork, innovation, and problem-solving abilities in real-world technical challenges.

Cyber Talent
Demonstrates your skills in cybersecurity, including threat detection, risk assessment, and protection against cyber threats.
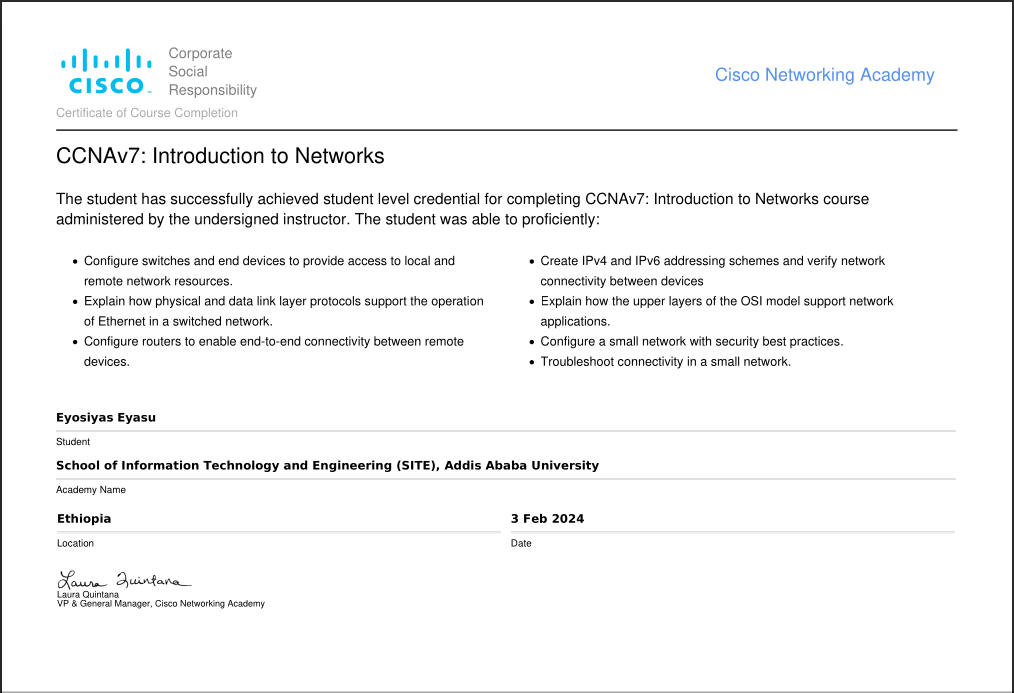
CCNA: Introduction To Networking
This course covers the fundamentals of networking, introducing topics like network models, IP addressing, Ethernet, and basic network configurations. It provides a foundation in networking concepts, devices, and protocols.
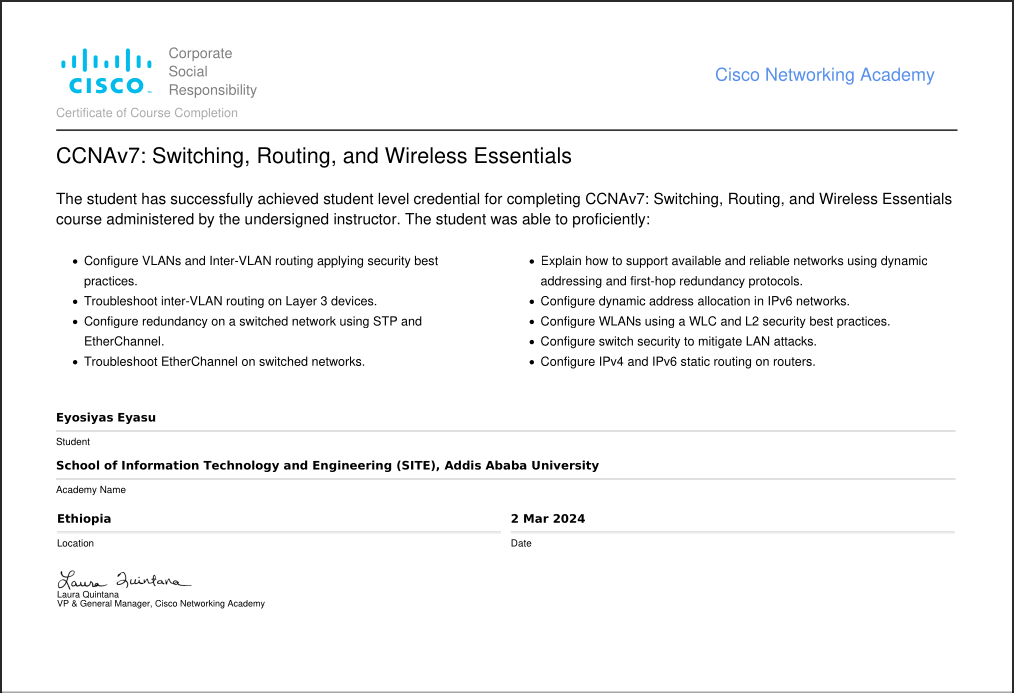
CCNA: Switching, Routing, And Wireless Essentials
This course covers the configuration and management of switches, routers, and wireless networks. It dives deeper into LAN and WAN protocols, VLANs, inter-VLAN routing, and network troubleshooting.
CCNA: Enterprise Networking, Security And Automation
Focuses on the architecture, security, and automation of enterprise networks. Topics include VPNs, routing protocols, network security, and the use of automation to manage and scale networks.